Hello friends : I've Posted Manual SQL Injection technique complete tutorial + Guide and method of SQL Injection. But do you know? instead of that long procedures and method you can also use Havij Automatic (Advance SQL Injection Tool). So here today I'll show you Website Hacking using Havij.
* What is Website Database ?
The Website Database is a collection of Information like Images, Login ID's, Password, Company Data, etc. That is all stored in a Server Database so that it can be easily acessed, managed and updated. In one view, databases can be classified according to types of content : Bibilographic, full-text, numeric, and Images etc.
What is Havij ?
Havij Pro is an advanced SQLi Vulnerability Exploiter, that can Exploit SQL Injection Vulnerability in Website and and get accessed into website database. Havij is Automatic Advance SQLi Tool.
How to hack Website using Havij ?
First of all there is nothing hard in this tutorial or damn steps to be followed - Just read it once - simply. But if you really want to learn SQL Injection then try to do it manually instead of using any tools..! As i showed in Latest Tutorial SQL Injection Website Hacking techniques.
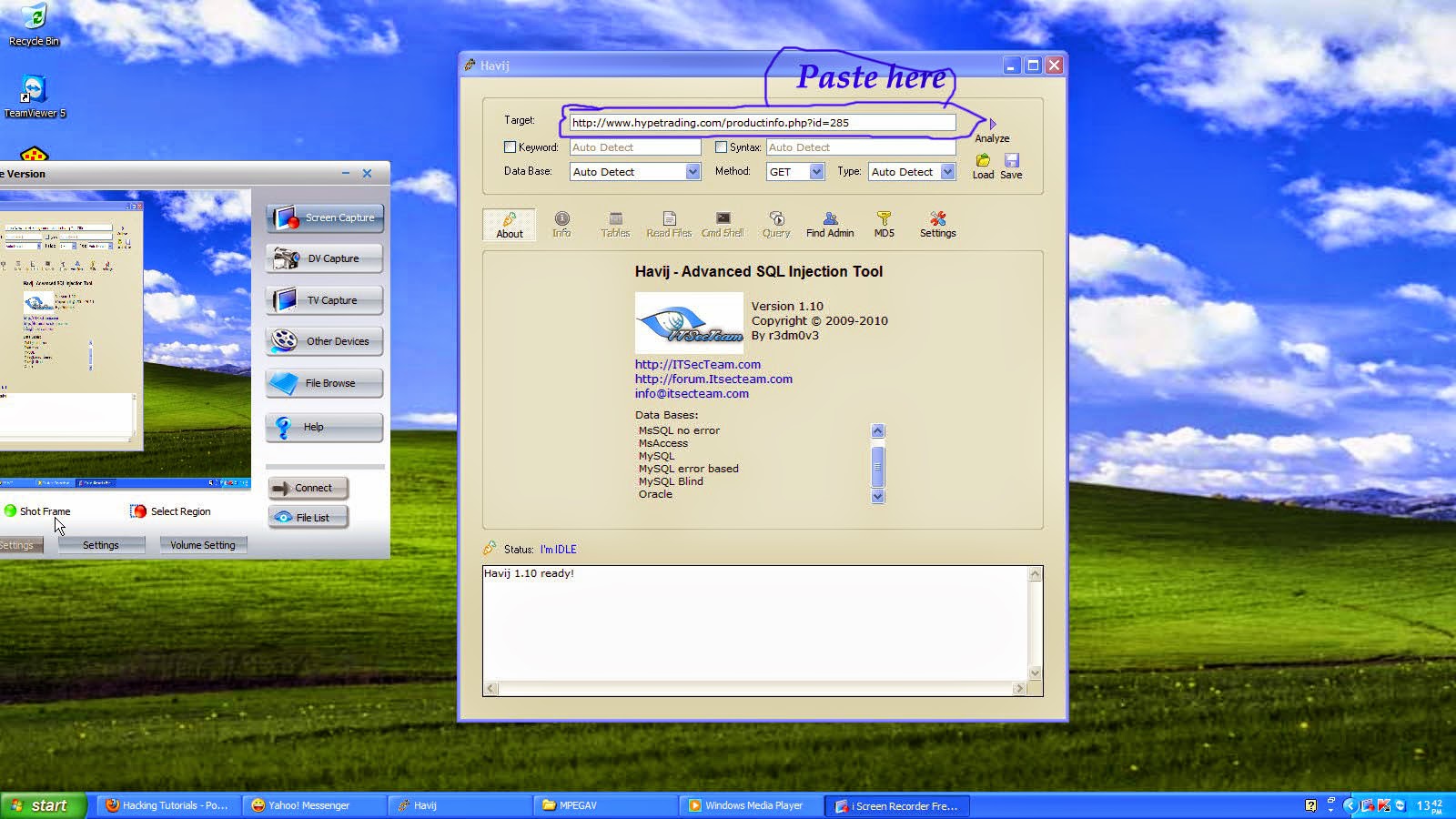
Now Let's start
Open havij and copy and paste infected link as shown in figure
Now click in the "Analyze"
Then It shows some messages there....Be alert on it and be show patience for sometime to find it's vulernable and type of injection and if db server is mysql and it will find database name.Then after get it's database is name like xxxx_xxxx
Then Move to another operation to find tables by clicking "tables" as figure shown.Now click "Get tables" Then wait some time if needed
After founded the tables ,you can see there will be "users" Put mark on it and click in the " get columns " tab as shown in figure
In that Just put mark username and password and click "Get data"
Bingo Got now id and pass that may be admin...
The pass will get as md5 you can crack it also using this tool as shown in figure...
or search in google md5 decrypt and follow website
Requirements :
Havij Pro [Click to Download From Tool Box]
Vulnerable website [SQLi Vulnerable Website]








.jpg)











